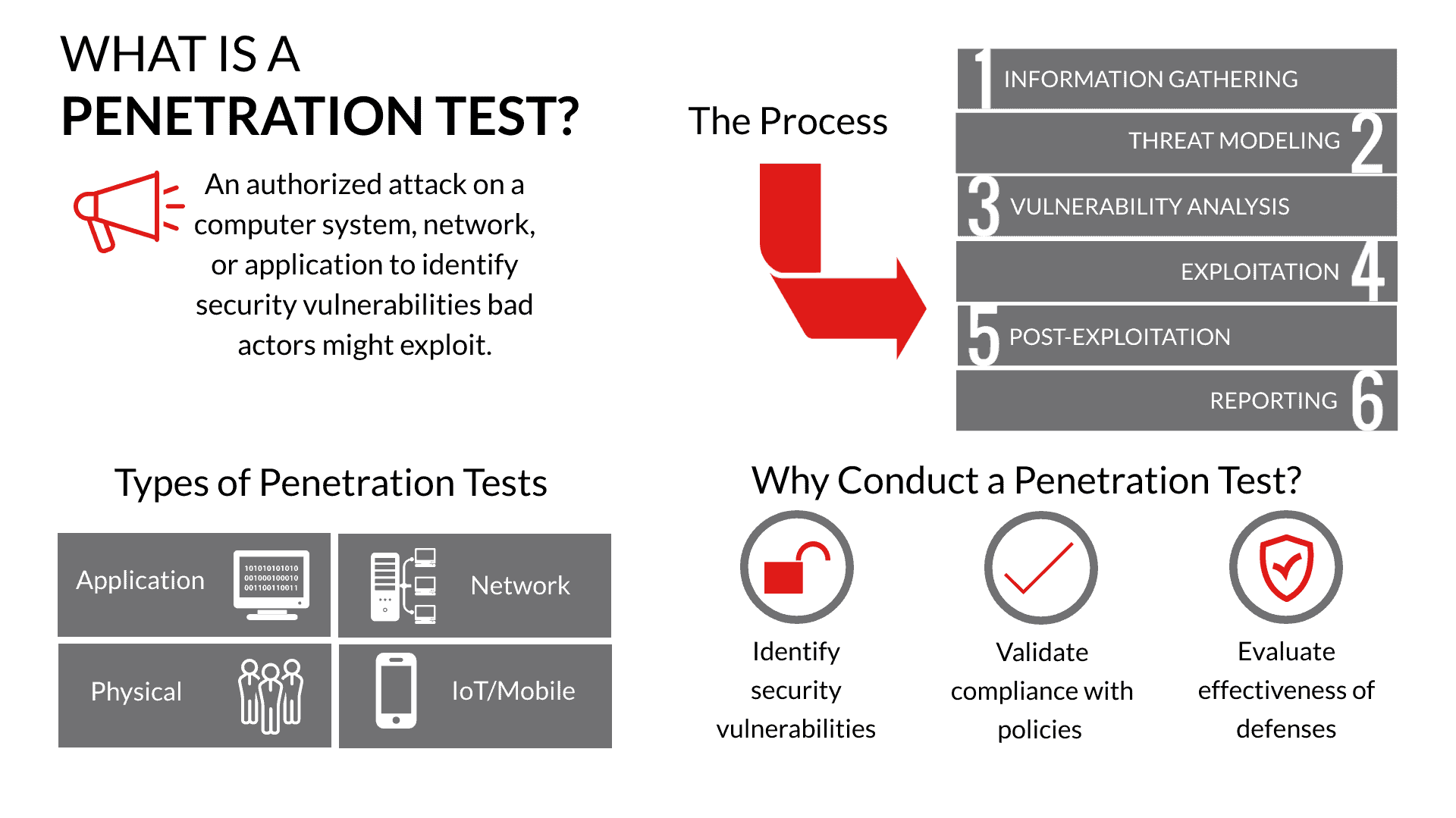
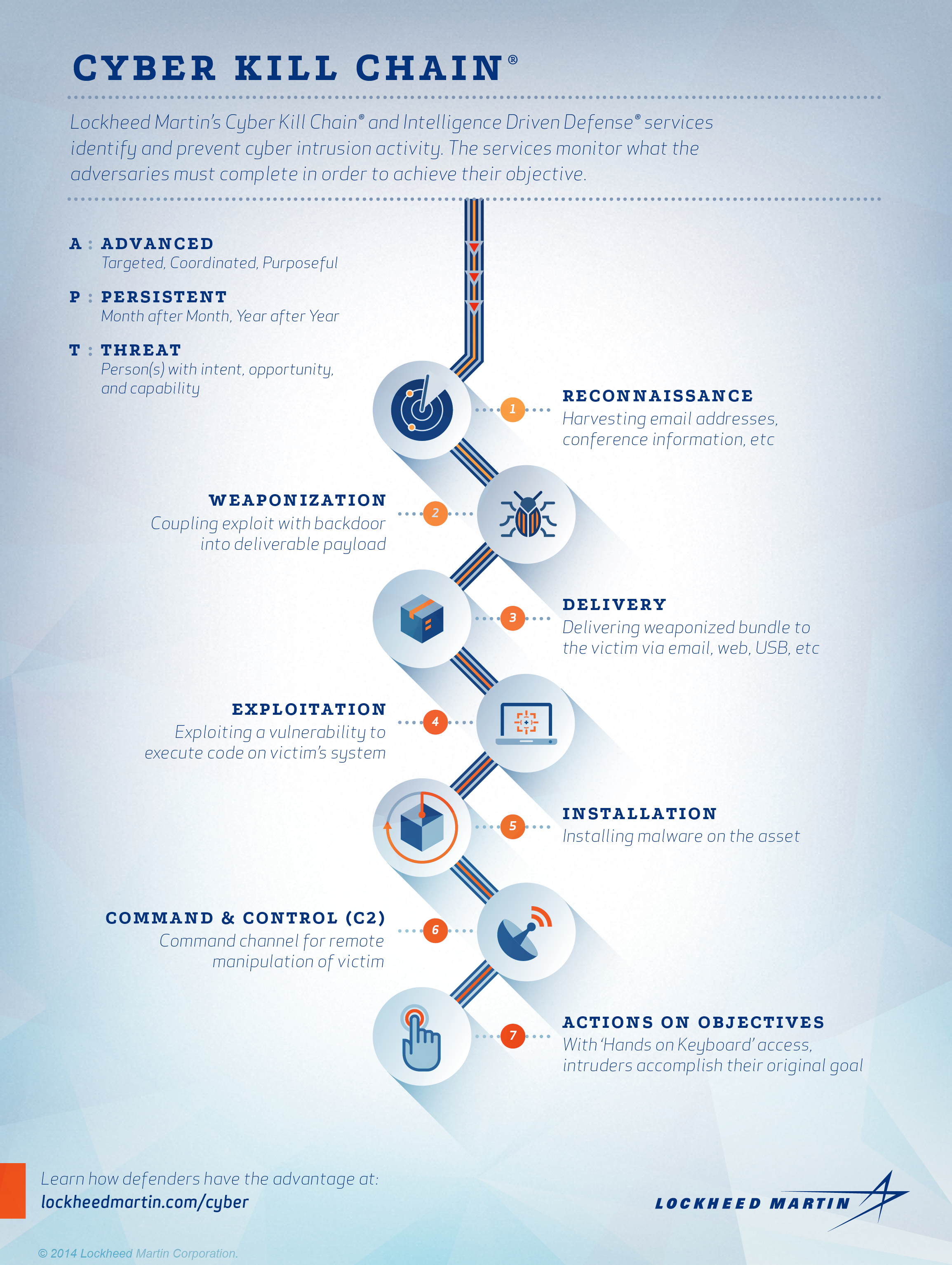
Denmark's Offensive Cyber Capabilities: Questionable Assets for Prestige, New Risks of Entrapment - Scandinavian Journal of Military Studies

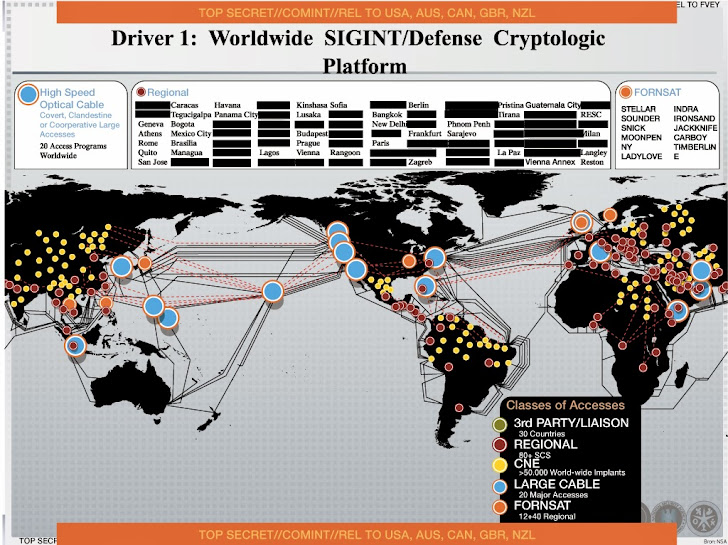
People's Republic of China Cyber Warfare and Computer Network Exploitation Capability Report | Public Intelligence
Example: Exploiting a typical Windows Domain network - Bob's Tech Talk - Bobs Tech Talk News and Reviews

The Exploitation of Instant Messaging to Monitor Computer Networks Using XMPP: A Study Focuses on School Computer Labs | Semantic Scholar

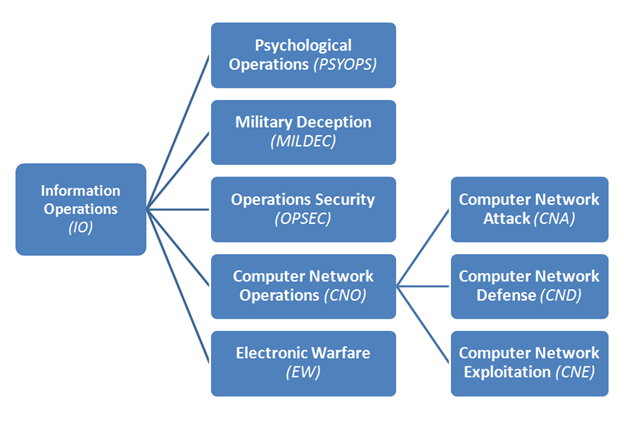
A schematic view of how Computer Network Attack (CNA)/ Computer Network... | Download Scientific Diagram

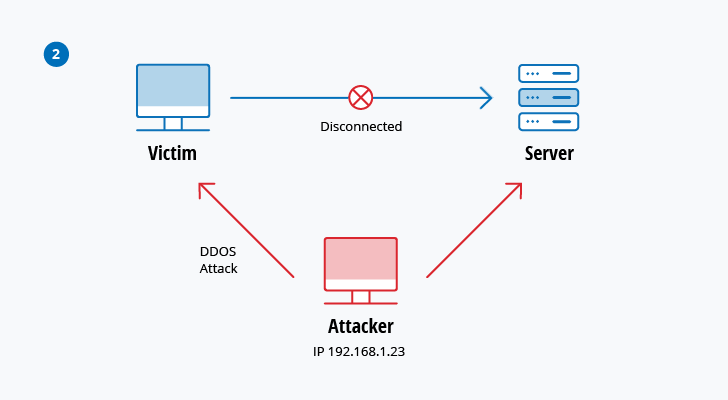
A comprehensive review study of cyber-attacks and cyber security; Emerging trends and recent developments - ScienceDirect

A comprehensive review study of cyber-attacks and cyber security; Emerging trends and recent developments - ScienceDirect

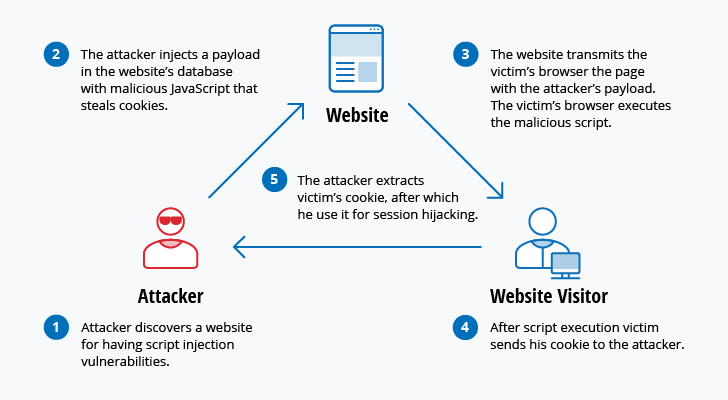
/cloudfront-ap-southeast-2.images.arcpublishing.com/nzme/KTYPA66EVVGTLICWV2IJP2OS4U.jpg)